How to Identify Malicious Emails
Most infections we are tasked to cleanup have taken advantage of the small window of opportunity a newly created or modified virus has to spread before anti-virus and anti-SPAM vendors have had a chance to identify it or update their filters to catch the new threat. To help protect yourself from these threats, here are some tips on how to identify and avoid potentially malicious emails.
Once you have read through all these tips, we recommend you test your ability to pick between malicious and legitimate emails using this Phishing IQ quiz provided by SonicWall.
- Check the “From” and “To” fields in the email. In particular look that the domain of the sender matches where you expect the message to be coming from. E.g. An email from Australia Post should have a from address “@auspost.com.au”. Also watch out for emails where you don’t see yourself in the “To” field or you see other unfamiliar email addresses in the “To” field. HOWEVER, similar to a traditional mail envelope, the “From” field can be faked by the sender and should not be trusted. So while it can be used to check for suspicious senders, you cannot trust an email just because the “From” shows it as being “@auspost.com.au”.
- Be weary of any email with attachments or links to download/view files, especially if they are unexpected. In particular emails claiming to contain invoices or advising that there is a package for you to collect or links to a webpage that requests you “login” before being granted access to view a file.
- Check for spelling or grammar mistakes. This can be an indication they were not sent from an official source.
- Check the greeting. Be weary of emails that use a generic greeting or one that can be related directly back to your email address (Dear Sales).
- Watch out for urgent or threatening language. Things such as “transaction blocked”, “account is overdue” or “account suspended”. The idea is to try and invoke a response based on fear, anxiety or confusion and have you click an attachment or link without assessing the risks first.
- Do not follow, but check all links in the email. By hovering the mouse over a link you should be able to see where the link is pointing to. Sometimes the text in the email or webpage that displays the link can be different to the address the link points to. NOTE: This advice is primarily to check for an indication the email is malicious. It is good practice to avoid following any link from any email (even “trusted” sources) where possible, especially for banking or any other website where you are expected to enter login or other sensitive information. Instead open up the webpage by typing the address into the web browser manually or use a bookmark that has been previously setup. Below is an example from a real phishing email that we received. You can see that the link is disguising itself as a link to https://banking.westpac.com.au, but actually is pointing to somewhere different.
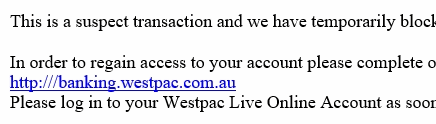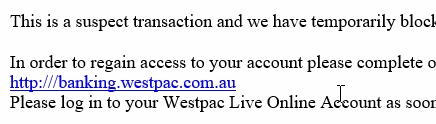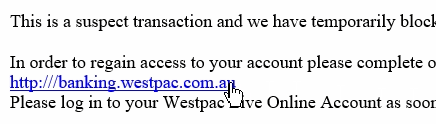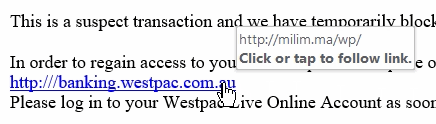
Sometimes the domain name itself is an attempt to disguise the link and you will need to decipher the link further to check its authenticity. Domain names are the bit contained between the https:// and the first /. The domain name indicates which server your browser will connect to, so it is important to verify the domain name to be sure you are not being taken to an unknown server hosting malicious content. By breaking up a domain name at each period, you can determine whether the link is legitimate or actually represents a subdomain of a malicous website.
For example, here is another malicious link: https://auspost.com.au.do-not-click-me.com/blahblahblah/ (different parts of the URL are highlighted for easier explanation). To verify the authenticity of this link we need to verify that the website’s domain name will take us to the website we expect. We do this by working right to left from the first / after the https://. If there is no / in the link, we work backwards from the very end of the URL. What you should find is the domain name of the website you are checking for immediately to the left of the first /. For the Australia Post website we expect to see auspost.com.au/, but what we find is do-not-click-me.com/ instead. We do see the domain name contains auspost.com.au. in it, but this comes to the left of do-not-click-me.com/. This indicates the auspost.com.au. part of the domain name is really a subdomain of do-not-click-me.com and will link to a server that is really under do-not-click-me.com‘s control.
It is important to look for the first / and work backwards from there. This link (https://do-no-click-me.com/austpost.com.au/blahblahblah/) has austpost.com.au/ in the URL, and the austpost.com.au is immediately before a slash, but it is not between the https:// and the first /. Being to the right-hand side of the first / means that it is not part of the domain name (https://do-no-click-me.com/) and this URL will link to a server that is under do-not-click-me.com‘s control.
